What Is Phishing: How It Works and How to Protect Yourself
Introduction: Why understanding what is phishing matters
Phishing is a common and persistent cyber threat that targets individuals, businesses and public organisations. Understanding what is phishing is important because it remains one of the simplest routes for criminals to gain access to credentials, financial information and sensitive data. As online services become more central to daily life, recognising phishing attempts helps reduce fraud, protect personal privacy and limit operational disruption.
Main body: How phishing works and common forms
Definition and tactics
Phishing is a form of social engineering in which attackers send deceptive communications—often by email, text message or telephone—to trick recipients into revealing information or performing actions that benefit the attacker. Messages commonly imitate trusted brands or colleagues, use urgent language and include links or attachments that request credentials or download malware.
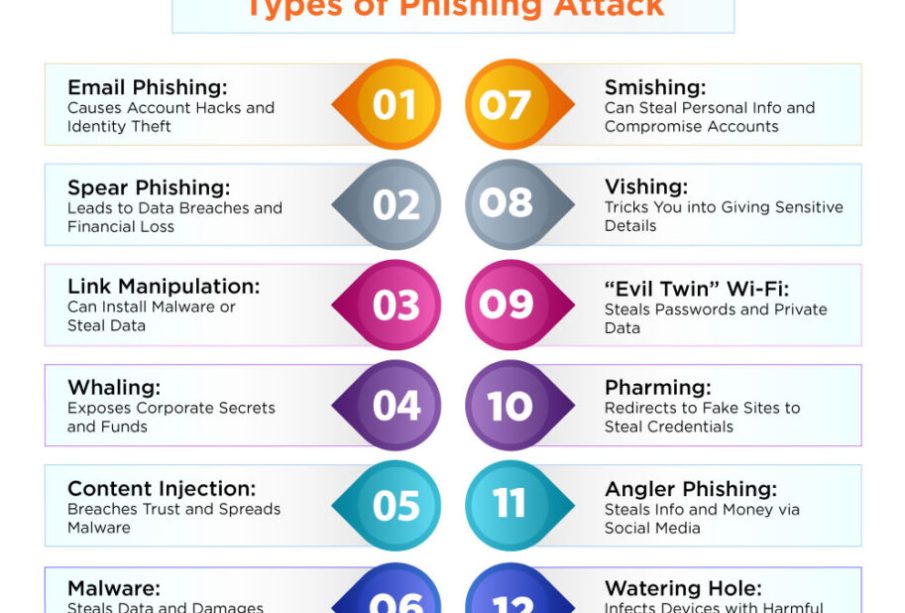
Common types of phishing
• Email phishing: Bulk or targeted emails that mimic banks, services or employers.
• Spear phishing: Tailored messages aimed at a specific person or organisation, using personal details to increase credibility.
• Smishing: Phishing via SMS/text messages that include malicious links or requests.
• Vishing: Voice calls that impersonate legitimate organisations to extract information.
• Pharming: Redirecting web traffic from legitimate sites to fraudulent ones, often by compromising DNS or local devices.
Signs of a phishing attempt
Typical warning signs include unexpected requests for credentials or money, poor spelling or grammar, mismatched sender addresses, links that do not match displayed text and unusual attachments. Genuine organisations rarely ask for passwords or payment details via unsolicited messages.
Impacts and immediate steps
Successful phishing can lead to credential theft, unauthorised financial transactions, data breaches and ransomware incidents. Immediate responses include not interacting with the message, verifying the sender through a trusted channel, changing compromised passwords and reporting the attempt to your organisation’s IT team or relevant authorities.
Conclusion: Outlook and practical advice
Phishing remains a leading entry point for cybercrime and is evolving with techniques such as deepfake audio and personalised social engineering. Individuals and organisations should adopt layered defences: user awareness training, multi-factor authentication, up-to-date software, reputable anti-phishing tools and clear reporting channels. By recognising what is phishing and applying basic precautions, readers can significantly reduce their risk of becoming victims.









