What is Phishing and How to Protect Yourself
Introduction: Why “what is phishing” matters
Understanding what is phishing is vital as online scams continue to target individuals and organisations. Phishing exploits trust to steal credentials, money or sensitive data. Its relevance spans personal security, workplace safety and public services — making awareness a key line of defence.
How phishing works
Common techniques
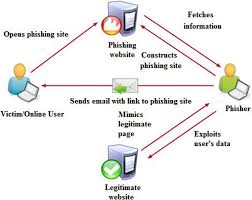
Phishing typically arrives via email, SMS (smishing), phone calls (vishing) or social platforms. Attackers impersonate reputable organisations or real contacts, often using urgent language or plausible-looking links and attachments. The primary goal is credential theft, unauthorised payments or installing malicious software.
Targeting and sophistication
Not all phishing is generic. Spear-phishing targets specific people or organisations using personal details gathered from social media or breaches. Business Email Compromise (BEC) is a related tactic where attackers trick employees into approving payments or sharing confidential information. Advances in technology, including automated tools and AI, have made messages more convincing.
Signs of a phishing attempt
Red flags include unexpected requests for passwords or payments, mismatched email addresses and display names, poor grammar, and links that lead to unfamiliar domains. Attachments with odd file types or prompting to enable macros are also common indicators of malicious intent.
Practical steps to protect yourself
Organisations and individuals can reduce risk through several measures: enable multi-factor authentication (MFA) on important accounts; verify suspicious requests by contacting the sender through an independent channel; hover over links to check destinations before clicking; keep software and devices updated; and use reputable security tools. Regular training and simulated phishing exercises help staff recognise evolving threats.
Conclusion: What readers should take away
Phishing remains one of the most prevalent cyber threats. Recognising what is phishing and adopting straightforward protections — vigilance, MFA, verification and software updates — significantly reduce exposure. Looking ahead, attackers are likely to grow more targeted and use more realistic content, so ongoing awareness and proactive defence will be essential for both individuals and organisations.









