Cybersecurity
Understanding the Coinbase Email Scam and How to Protect Yourself
Introduction In recent weeks, a significant surge in Coinbase email scams has raised alarms among cryptocurrency users. These phishing attempts pose serious ...Understanding the Potential UK VPN Ban: Implications and Reactions
Introduction The debate over the use of Virtual Private Networks (VPNs) in the UK has intensified, particularly in light of recent discussions ...Understanding the Role of Tor in Safeguarding Online Privacy
Introduction The importance of online privacy has become a critical issue in today’s digital age, especially with increasing surveillance and data collection ...The Growing Threat of Zero-Day Vulnerabilities
Introduction In our increasingly digital world, cybersecurity is a pressing concern for individuals and organisations alike. One of the most significant threats ...Understanding Zero-Day Vulnerabilities in Cybersecurity
Introduction to Zero-Day Vulnerabilities In today’s digital age, cybersecurity is more critical than ever. Among the various threats to information security, zero-day ...Concerns Over BBC Weak Password Security
Introduction In an era where cybersecurity has become a focal point for organisations and consumers alike, the importance of strong password practices ...Phishing Attacks: Recognising and Preventing Digital Fraud
Introduction Phishing attacks have become a prevalent form of cybercrime that targets individuals and businesses alike. These malicious attempts to acquire sensitive ...Significant Afghan Data Breach Exposes Sensitive Information
Introduction The recent Afghan data breach has raised significant concerns about data security and privacy in the region. Following the Taliban’s return ...M&S Cyber Attack: Implications for Data Security and Customers
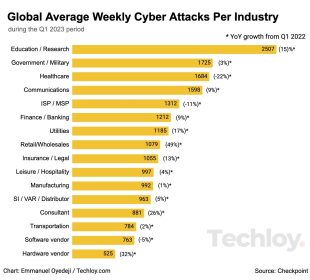
Introduction The recent cyber attack on Marks & Spencer (M&S), one of the UK’s leading retailers, has brought significant attention to the ...The Rising Threat of Cyber Attacks: What You Need to Know
The Importance of Cyber Security Today In an increasingly digital world, the prevalence of cyber attacks has become a significant concern for ...